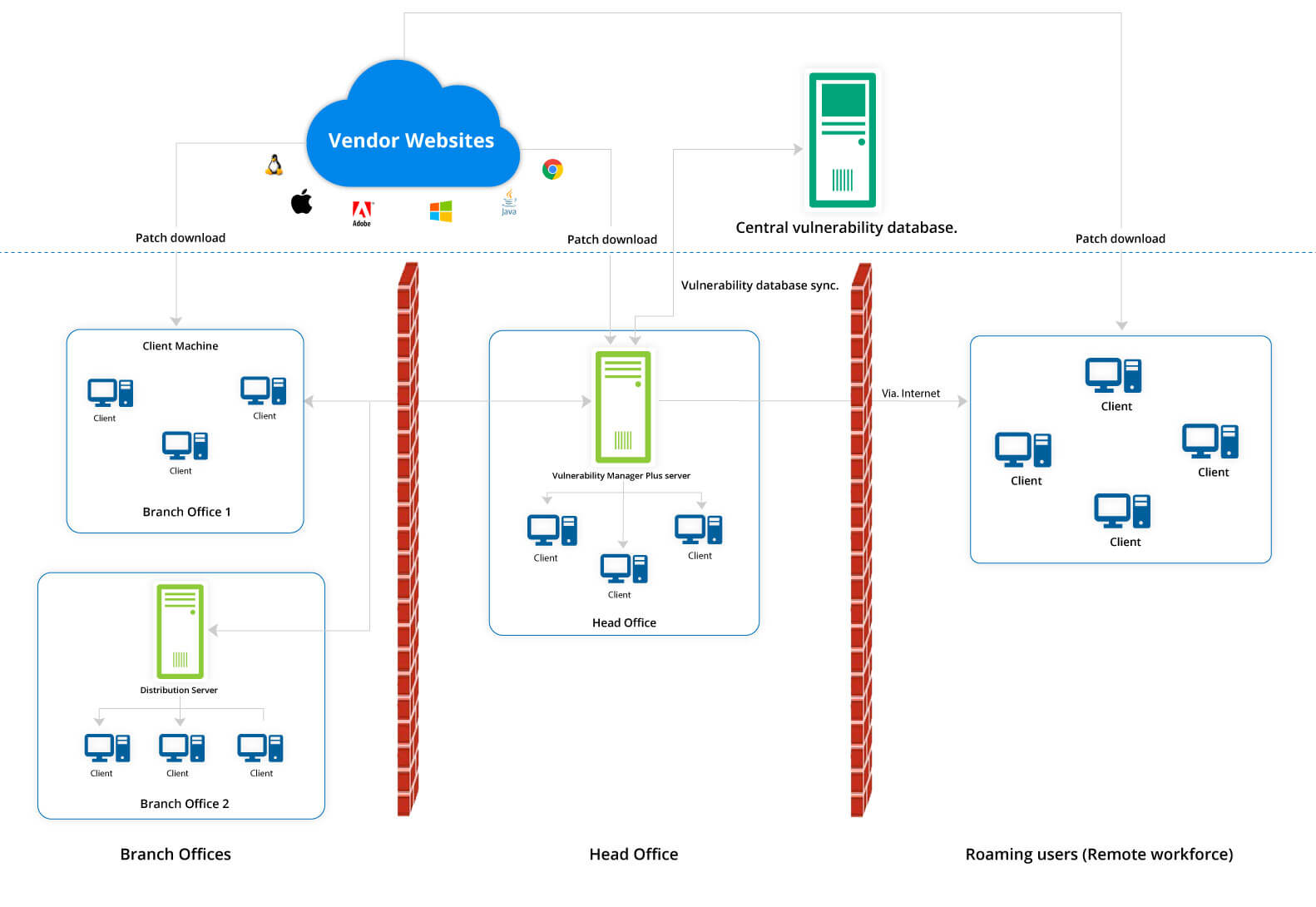
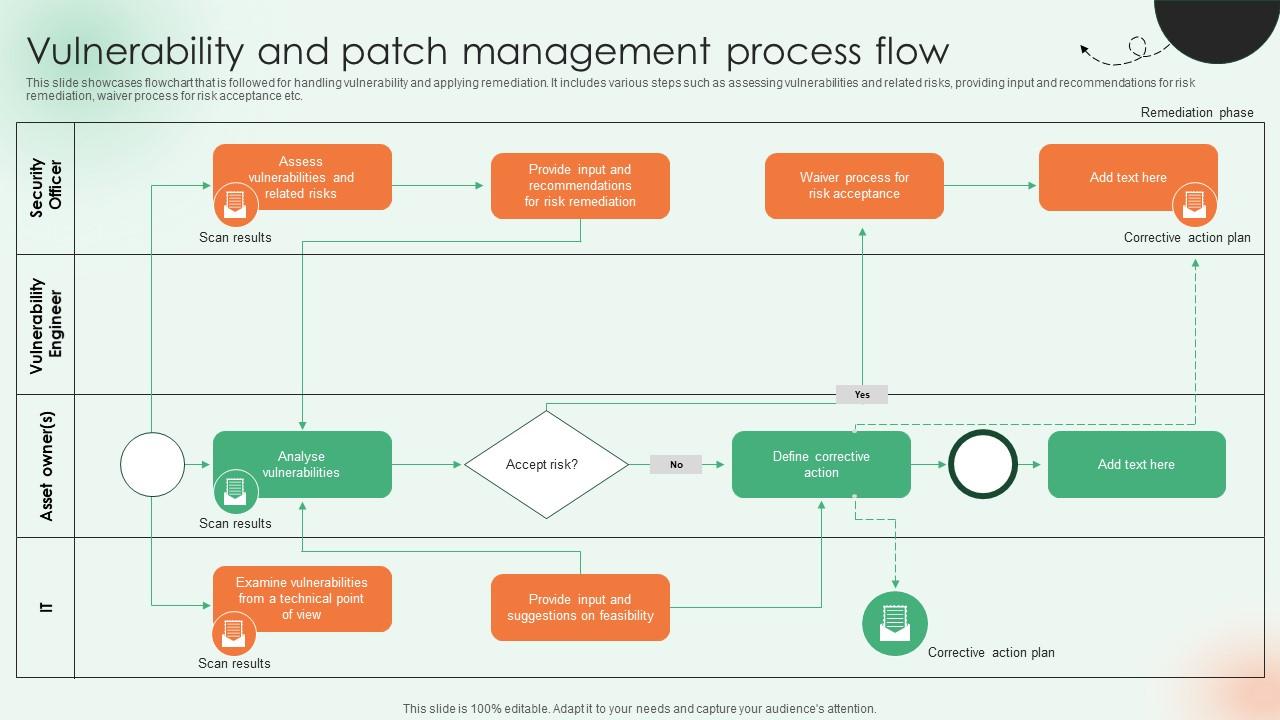
Définition de la gestion des vulnérabilités | Processus de gestion des vulnérabilités - ManageEngine Vulnerability Manager Plus
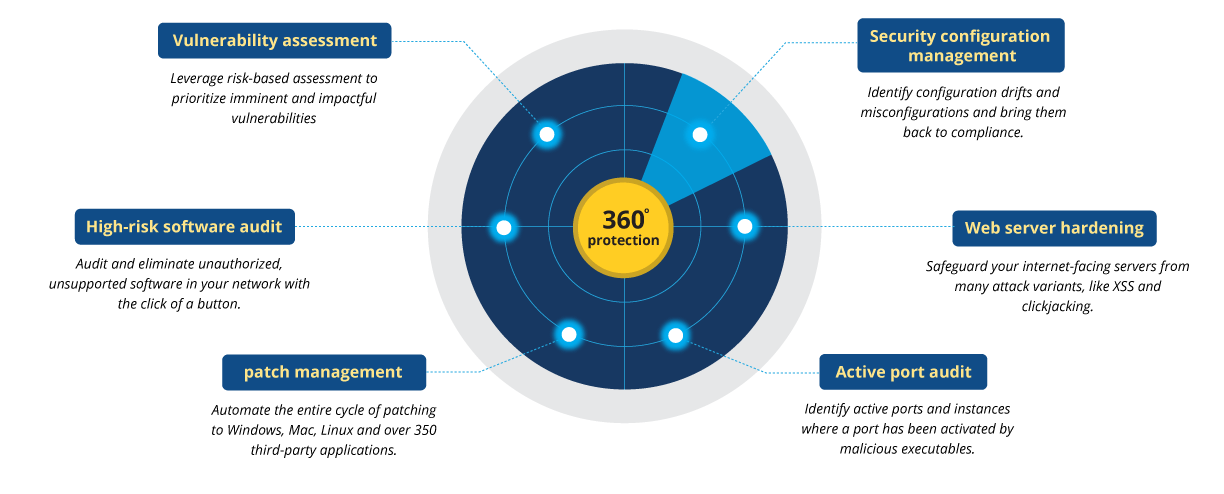
Définition de la gestion des vulnérabilités | Processus de gestion des vulnérabilités - ManageEngine Vulnerability Manager Plus

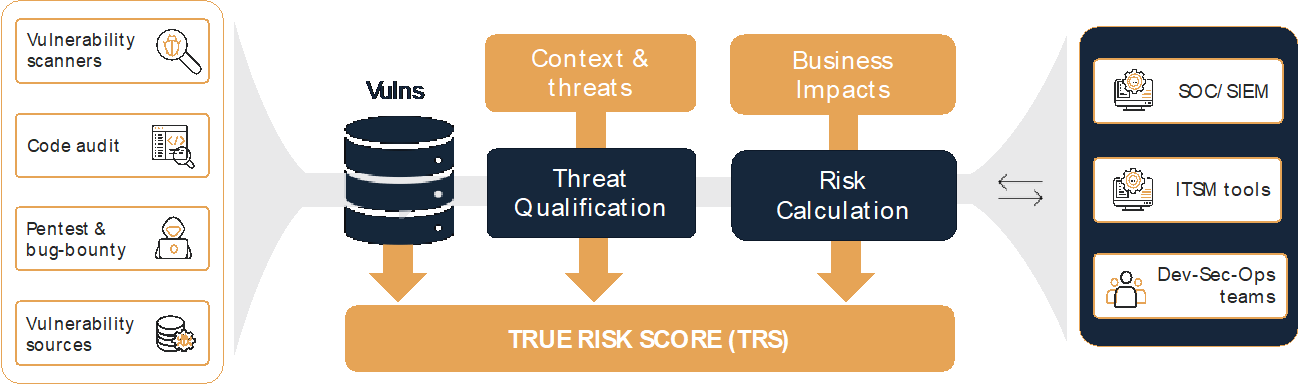
Vulnerable node identification method for distribution networks based on complex networks and improved TOPSIS theory - Jiang - IET Generation, Transmission & Distribution - Wiley Online Library

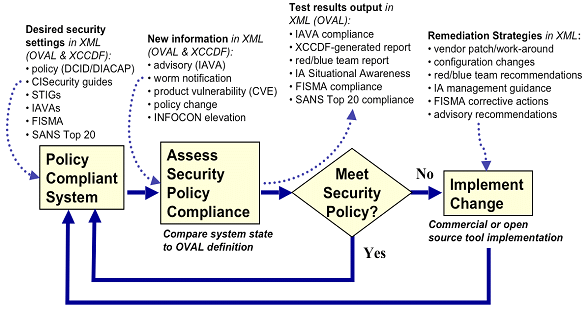
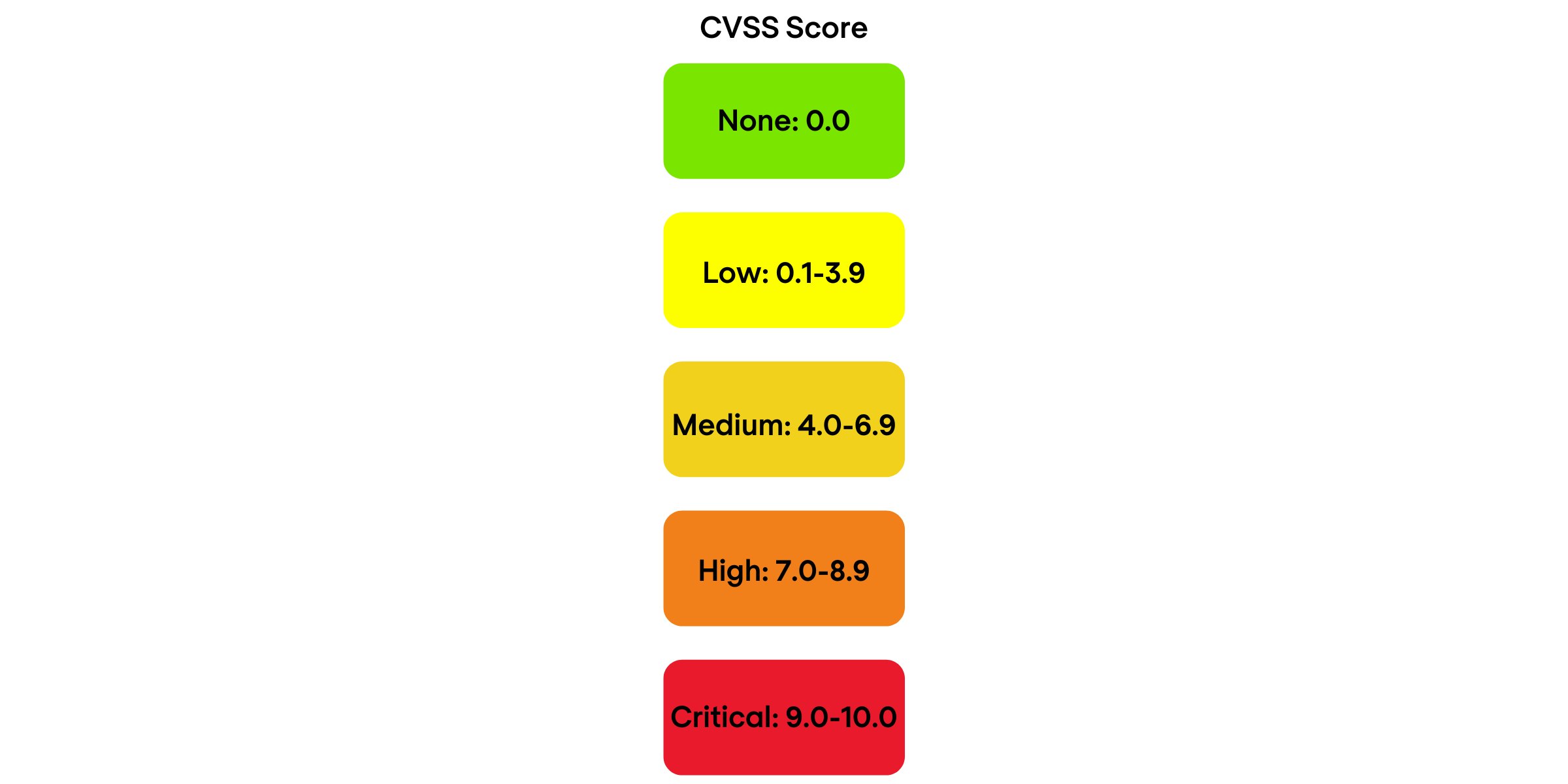
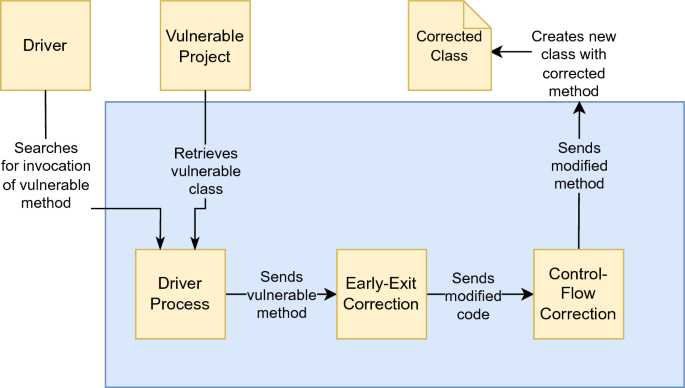
Managing vulnerabilities of information systems and information processing in enterprises – CISO practical point of view | TECH&DEV&SEC - technology, development & security



![Hikvision, HWG Deceive FCC About New Critical Vulnerability [Update: Hikvision Issues Correction] Hikvision, HWG Deceive FCC About New Critical Vulnerability [Update: Hikvision Issues Correction]](https://s.ipvm.com/uploads/embedded_image/dc2924c53291893666e336b8f2a820f913a59d9f396e0468ce9f1f0a3250306f/4fec498e-fe4a-4350-a53a-3ec6e029c335.webp)